Threat analysts at McAfee have discovered five Google Chrome extensions that can steal information about users’ web activity.existBefore being removed from the Chrome Web Store by Google, itsThe total number of downloads has exceeded 1.4 million.
These extensions provide functions such as enabling users to watch Netflix shows together, track some website coupons, and take screenshots of pages. But in addition to providing the above features, they also track the user’s web activity, and every user’s website visit information is sent to a server owned by the extension creator.The move is to insert code into visited e-commerce sites, modifying the site’s cookies so that extension authors can receive notification of any user purchasesAncillary payments.
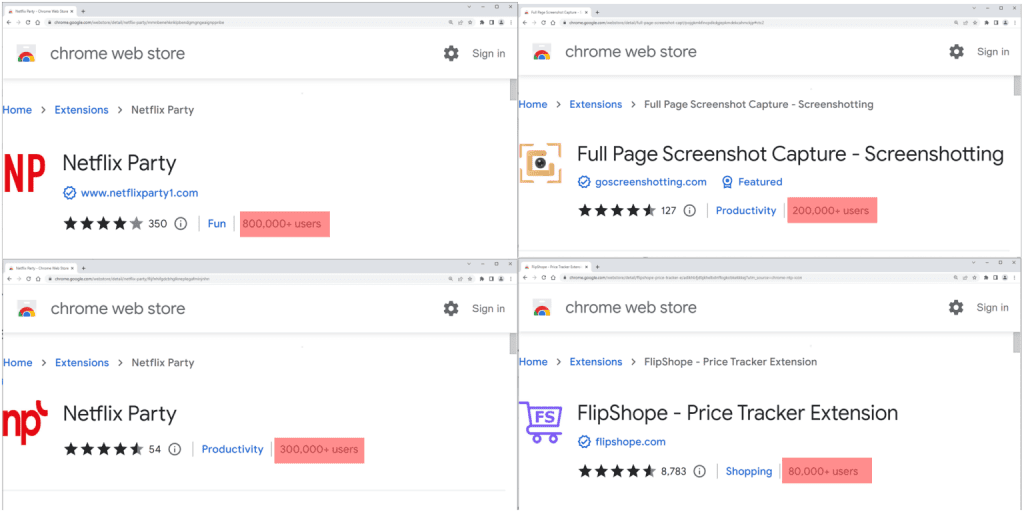
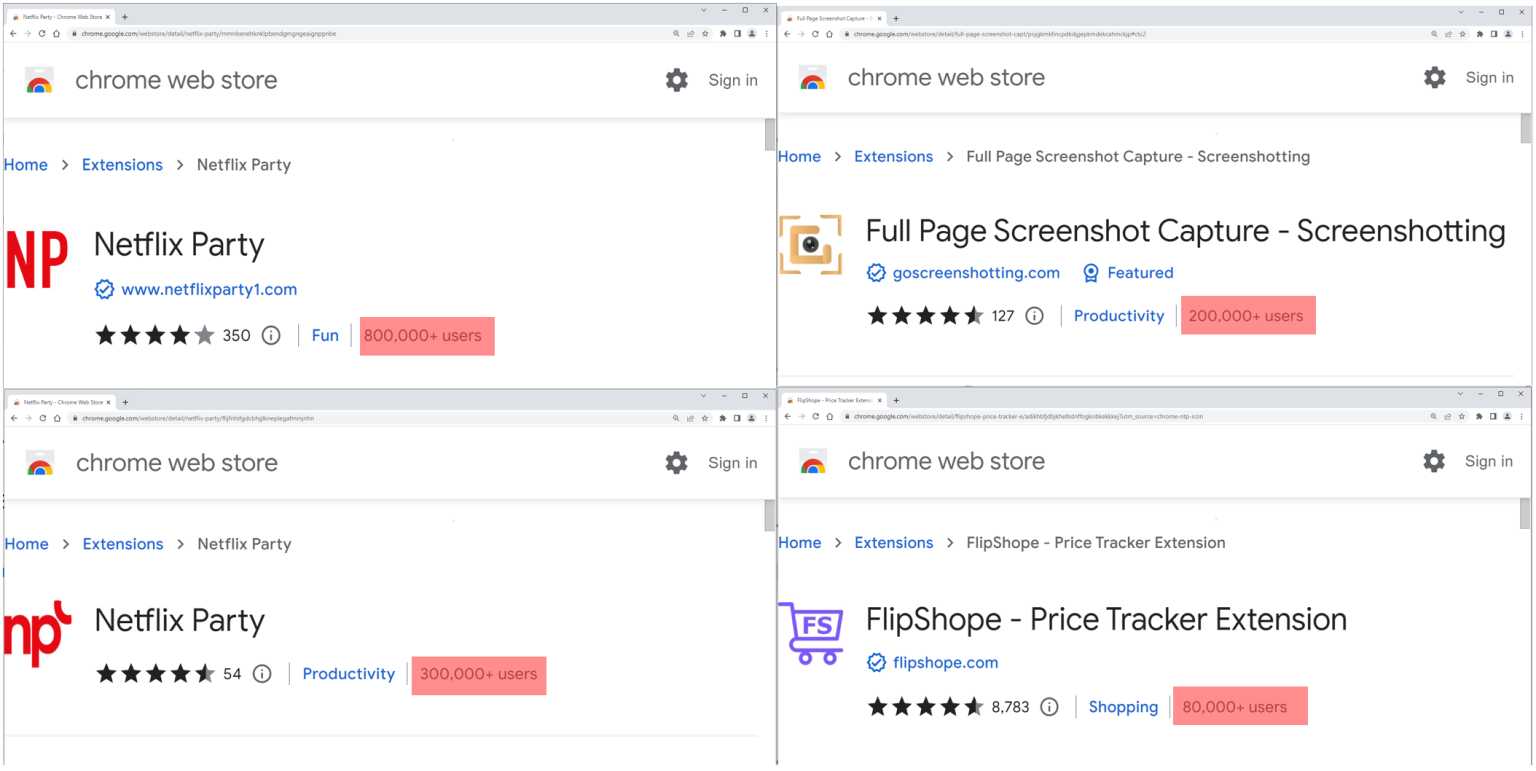
And extension users are unaware of the existence of this feature, nor of the privacy risk that every website they visit is sent to the extension author’s server.PlaceThe five malicious extensions discovered are as follows:
- Netflix Party (mmnbenehknklpbendgmgngeaignppnbe) – 800,000 downloads
- Netflix Party 2 (flijfnhifgdcbhglkneplegafminjnhn) – 300,000 downloads
- Full Page Screenshot Capture – Screenshotting (pojgkmkfincpdkdgjepkmdekcahmckjp) – 200,000 downloads
- FlipShope – Price Tracker Extension (adikhbfjdbjkhelbdnffogkobkekkkej) – 80,000 downloads
- AutoBuy Flash Sales (gbnahglfafmhaehbdmjedfhdmimjcbed) – 20,000 downloads
According to the introduction,All 5 extensions perform similar behavior.Web application manifest (“manifest.json” file)Prescribes how the extension behaves in the system, loads a multipurpose script (B0.js) that sends browsing data to an attacker-controlled domain (“langhort[.com”)。
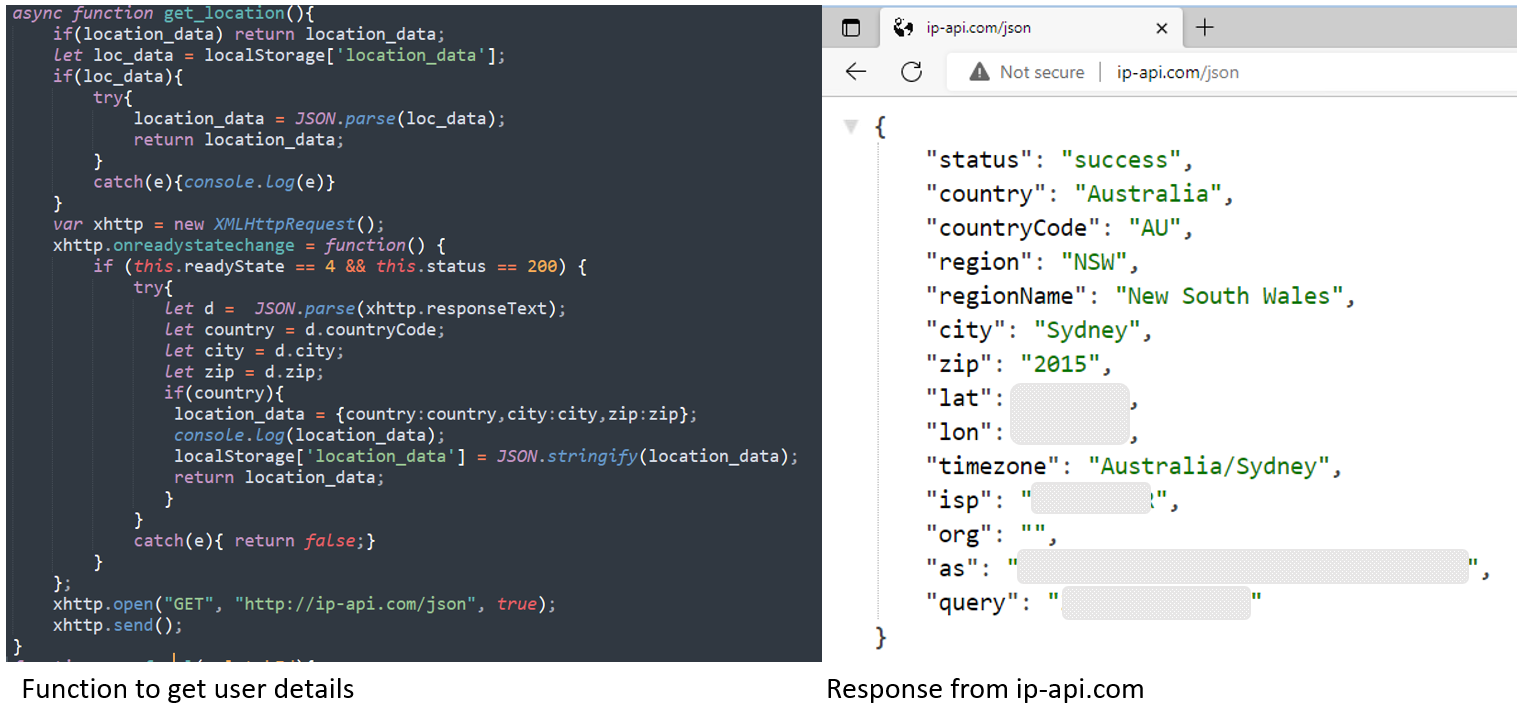
每次用户访问新 URL 时,数据都会通过 POST 请求传递。到达欺诈者的信息包括 base64 格式的 URL、用户 ID、设备位置(国家、城市、邮政编码)和一个 encoded referral URL。
如果被访问的网站与扩展作者有活动关系的网站列表中的任何条目相匹配,则服务器会使用两种可能的功能之一来响应 B0.js。
- “Result[‘c’] – passf_url”, the command script inserts the provided URL (referrer link) as an iframe to the visited website.
- “Result[‘e’] setCookie”, instructs B0.js to modify the cookie, or replace it with the provided cookie if the extension has been granted the relevant permission to do so.


Notably,To evade detection, analysis, and confuse researchers or wary users, some extensions include a time check before performing any malicious activity, delaying their installation for 15 days.

More details can be found on the official blog.
#Malicious #Chrome #Extension #Millions #Downloads #Tracks #User #Network #Behavior