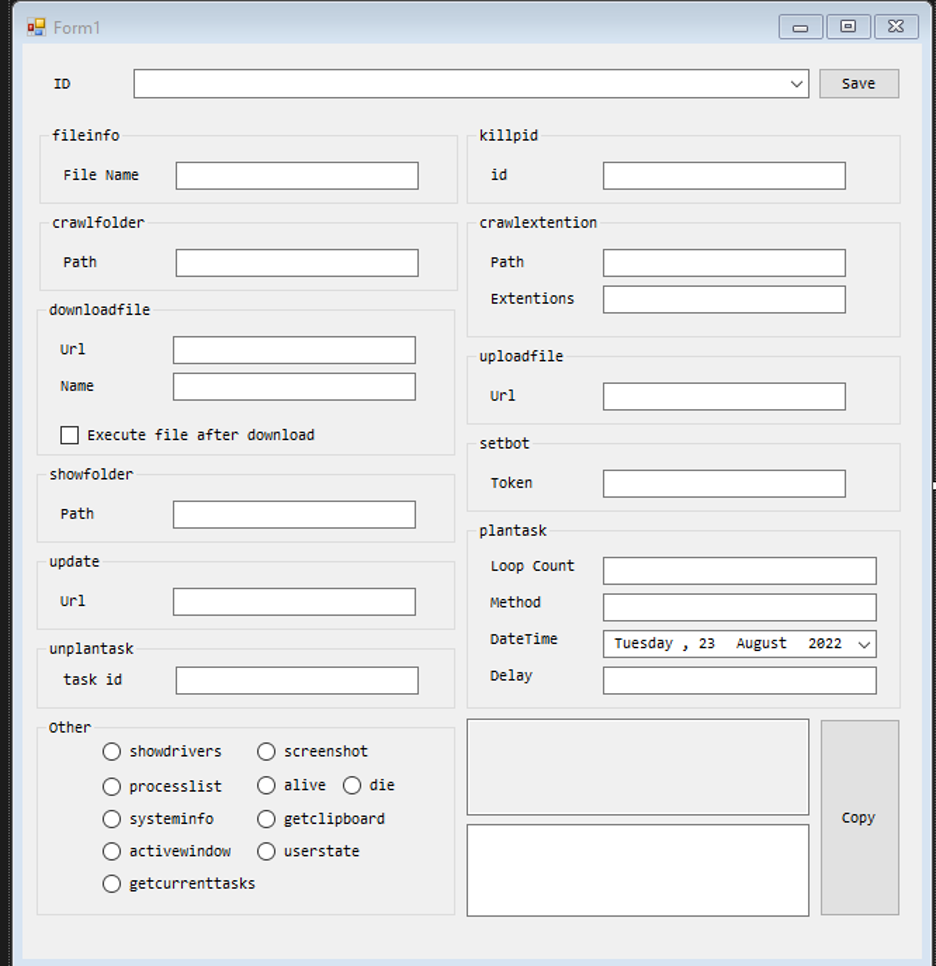
The developer of a new remote access Trojan (RAT) called CodeRAT has made its source code public on GitHub after malware analysts and developers questioned it about attacks using the tool.cyber security company SafeBreach ReportAllegedly, CodeRAT targeted Farsi-speaking code developers by using a Microsoft Word document containing a Microsoft Dynamic Data Exchange (DDE) vulnerability.
CodeRAT supports around 50 different commands related to file, process manipulation and screen capture, clipboard, file and environment information stealing, as well as commands for upgrading or installing other malware binaries.And has extensive monitoring capabilities for webmail, Microsoft Office documents, databases, social networking platforms, Integrated Development Environments (IDEs) for Windows Android and even personal websites like PayPal, as well as sensitive windows for tools like Visual Studio, Python, PhpStorm and Verilog .
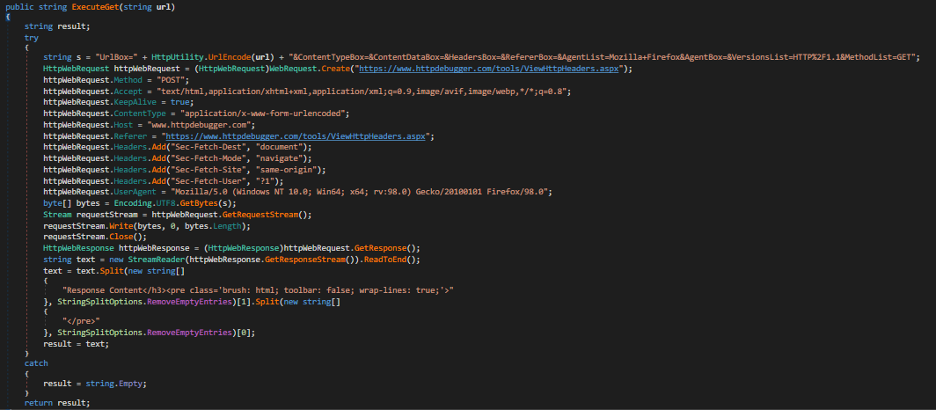
The way CodeRAT communicates is generic and very unique, supporting communication via Telegram groups using the bot API or USB flash drives. It can also run in silent mode, which includes not returning a report. CodeRAT uses an anonymous public upload site instead of a dedicated C2 server, and uses anti-detection techniques to limit its usage to 30 days. Additionally, it will use the HTTP Debugger website as a proxy to communicate with its C2 Telegram group.
By the time the researchers contacted the malware developer, its malicious activity had stopped abruptly; but despite this, BleepingComputer noted that CodeRAT may become more popular now that the author has made the source code public.
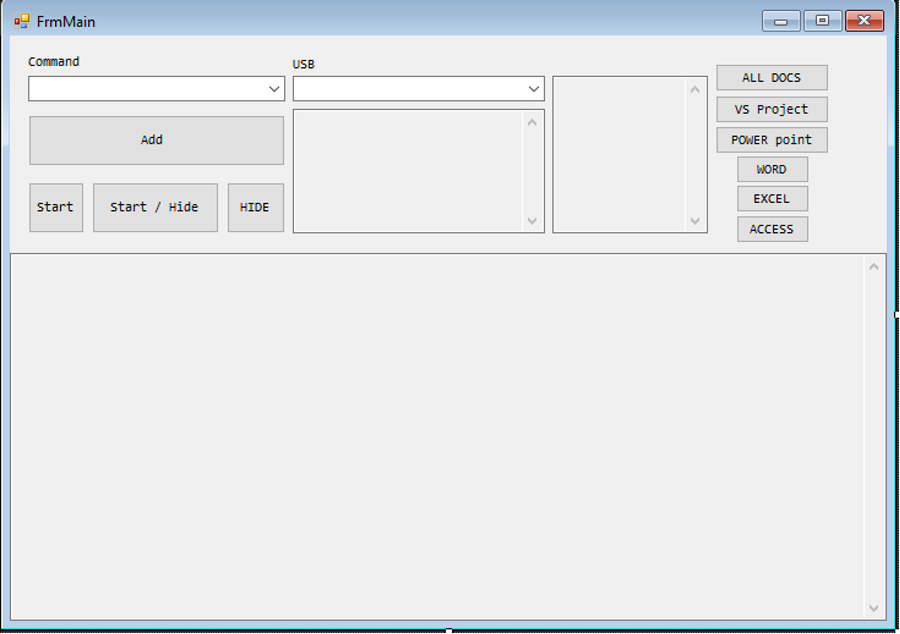
Attackers can generate commands through UI tools that build and obfuscate commands, and then transmit them to malware using one of three methods:
- Telegram bot API with proxy (no direct request)
- Manual mode (includes USB option)
- Commands stored locally in the “myPictures” folder
The same three methods can also be used for data exfiltration, including individual files, entire folders, or targeting specific file extensions.
If Telegram is banned in the victim’s country, CodeRAT provides an anti-filtering feature that establishes a separate request routing channel to help bypass the block.
The malware is said to persist between reboots without making any changes to the Windows registry, but SafeBreach did not provide any details about this functionality. CodeRAT comes with powerful features that are likely to attract other cybercriminals.
#Malware #Developer #Open #Sources #CodeRAT #Exposure