ginv sso is a pure background single-point management system, which is used to solve the account login and authorization management of one or more background management systems.ginv ssoThe front-end and back-end separation technologies are used by default. The server is developed with golang, based on the go-zero framework; the front end is developed with vue3, based on ant design vue.
ginv ssoThere are three systems of auth, ssoms, and gateway, which have the following functions respectively:
auth: 负责系统登录验证、页面权限验证、接口授权验证
ssoms: 负责角色、用户管理、系统和菜单管理、角色授权
gateway: 登录登出页面、负责接入请求和转发请求
ginv ssoMultiple background systems must be subdomains under the same domain name. The purpose of this is to use secure httpOnly cookies for user identification across multiple systems.
feature
- According to the api rules created by goctl of go-zero, the request is checked for permission in resetful style
- The front end can generate ts through the api file of goctl, request the gateway, and improve the work efficiency of the front end
- Menu & operation uses uuid as the unique key instead of self-incrementing id, which is convenient for cloning menus in different environments or systems
- Menu & Actions highlight search results
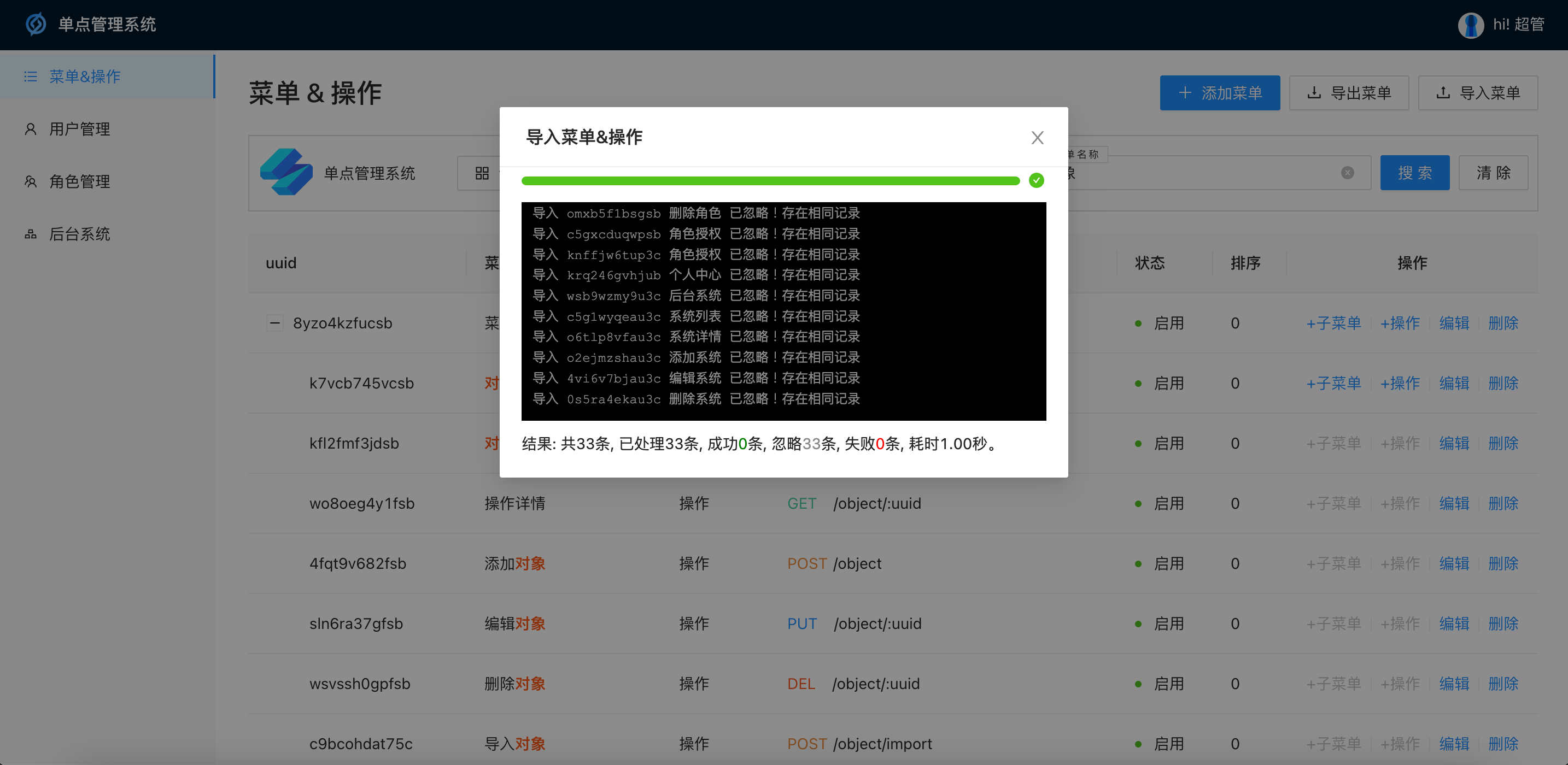
- Batch import results return multiple statuses and import information, ignoring duplicate records
about ssoms
ssoms is a single sign-on management background, it has the following functions
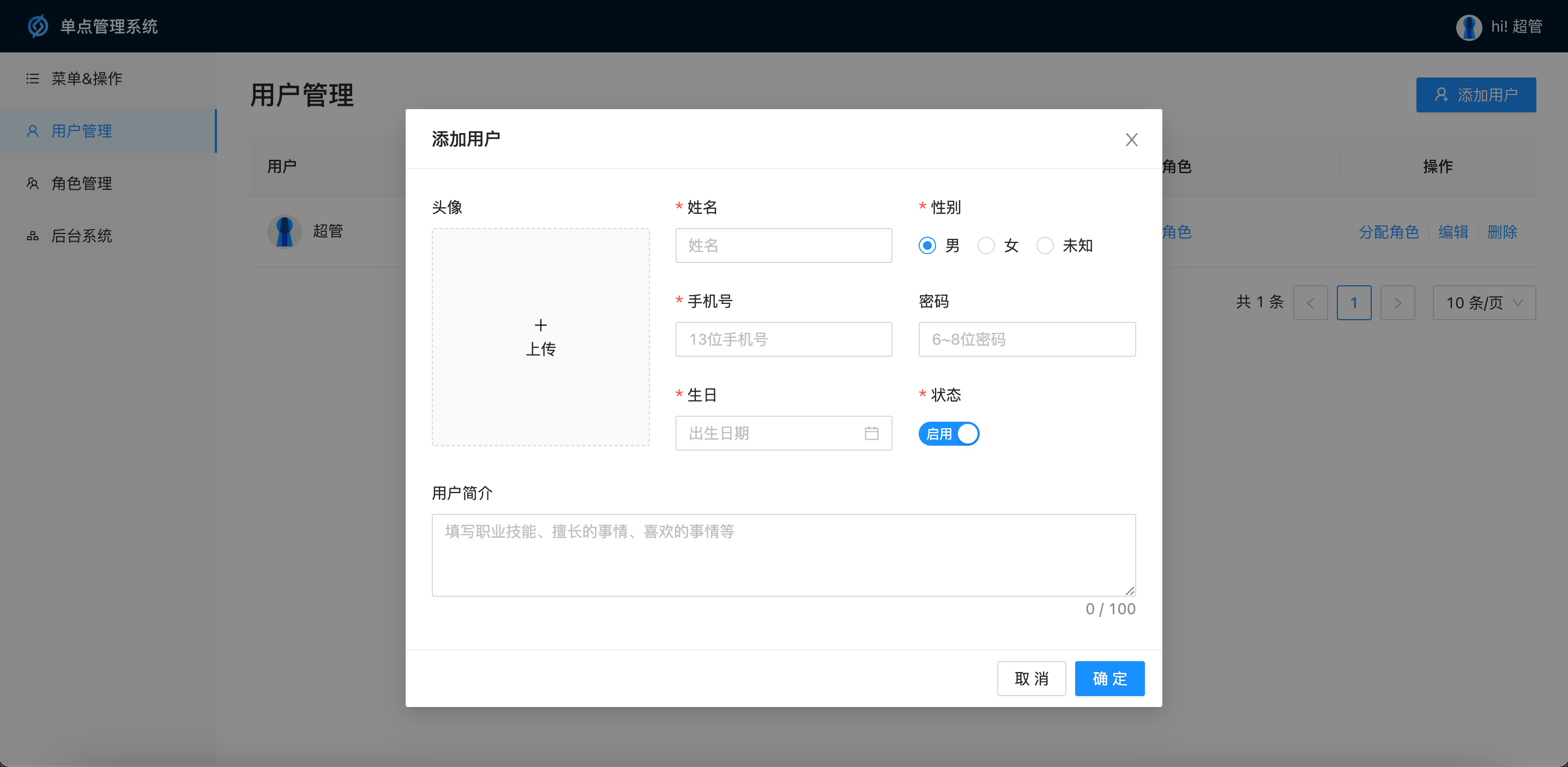
User Management: Addition, deletion and modification of basic user information, role assignment
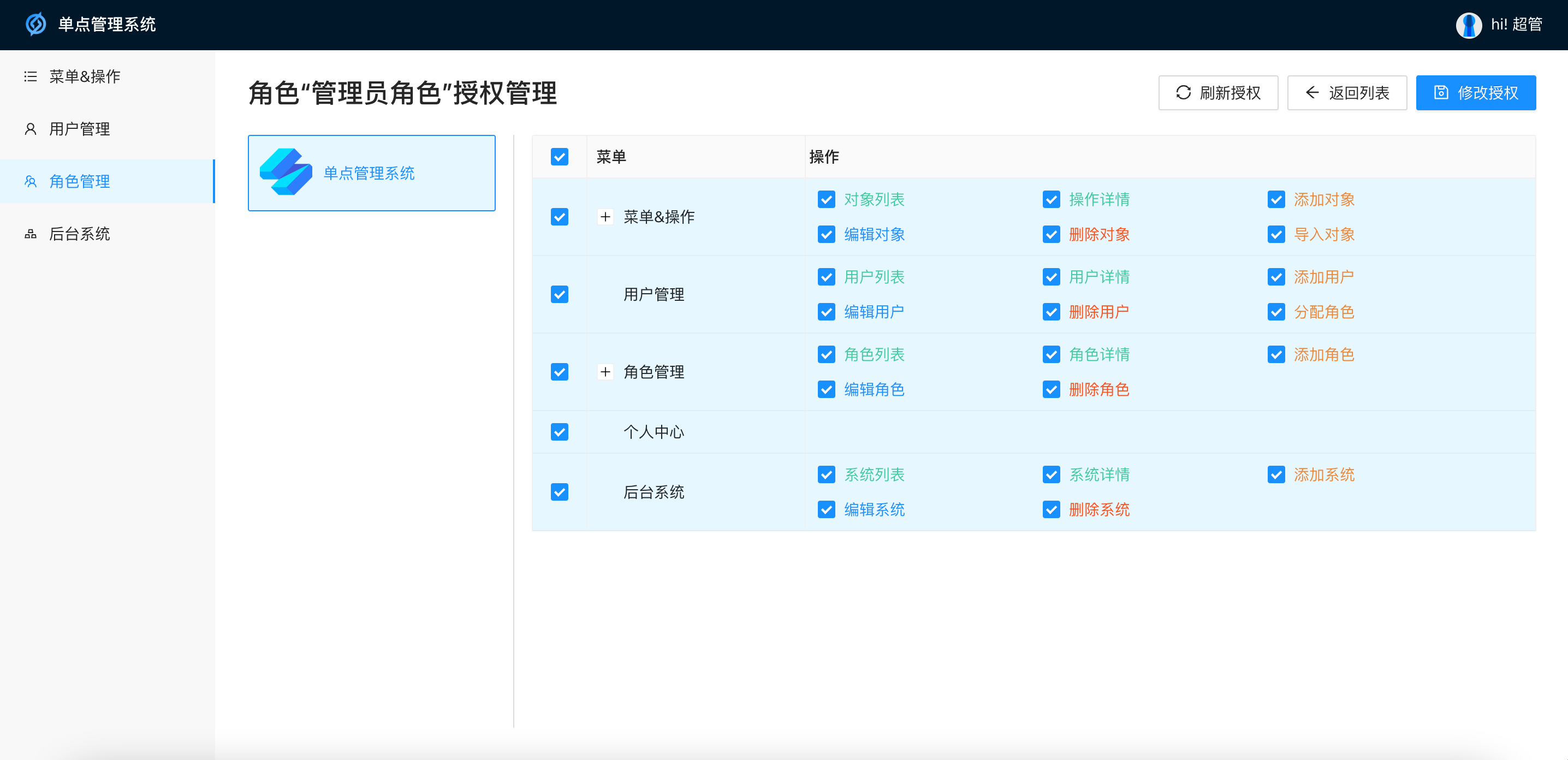
Role management: Basic operations of roles, assigning users, menus of roles & assignment of operation rights
System Management: Manage backend systems using single sign-on
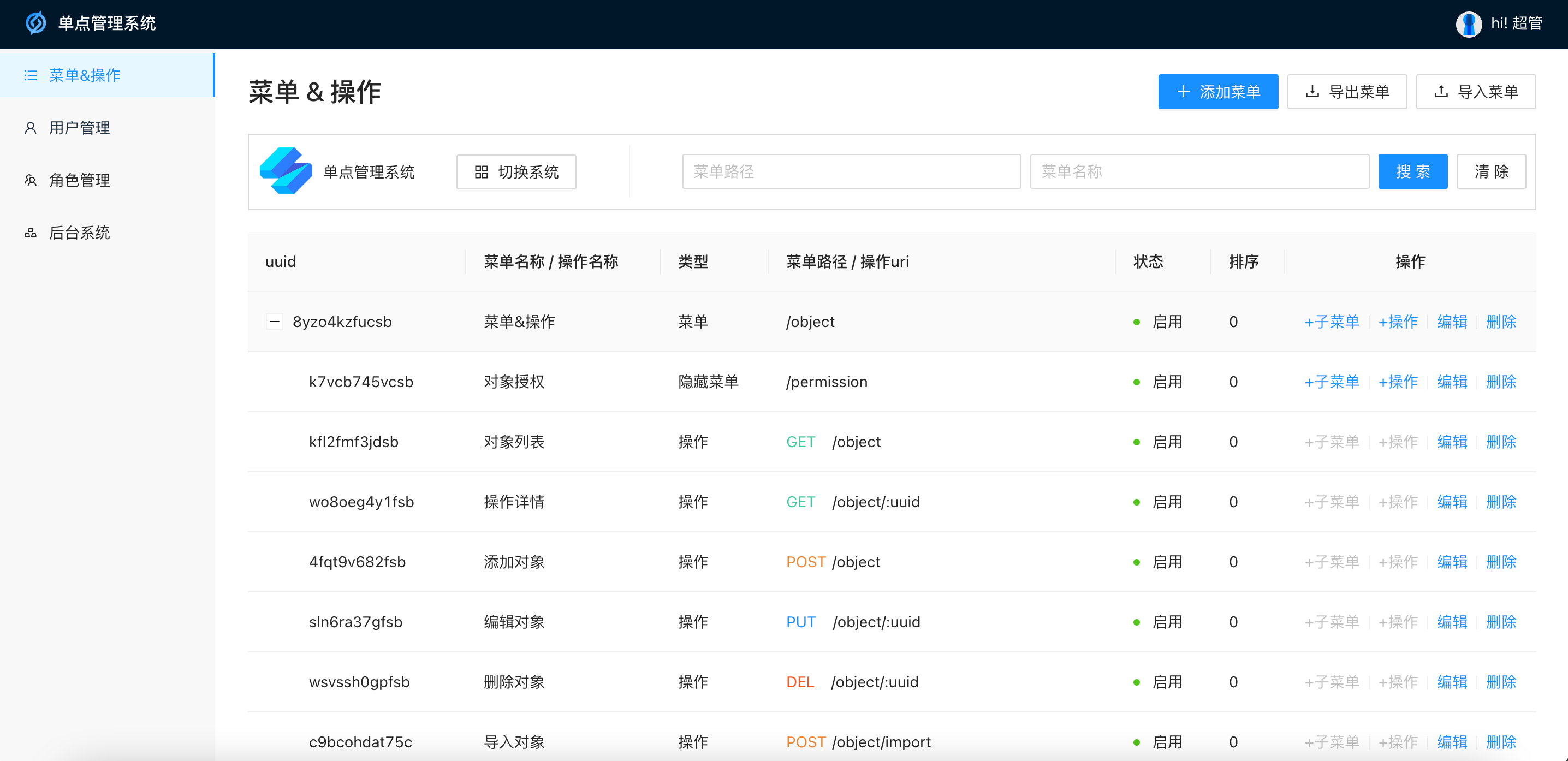
Menu management: Configure the menu & operation of the system, support highlight query, batch import and export
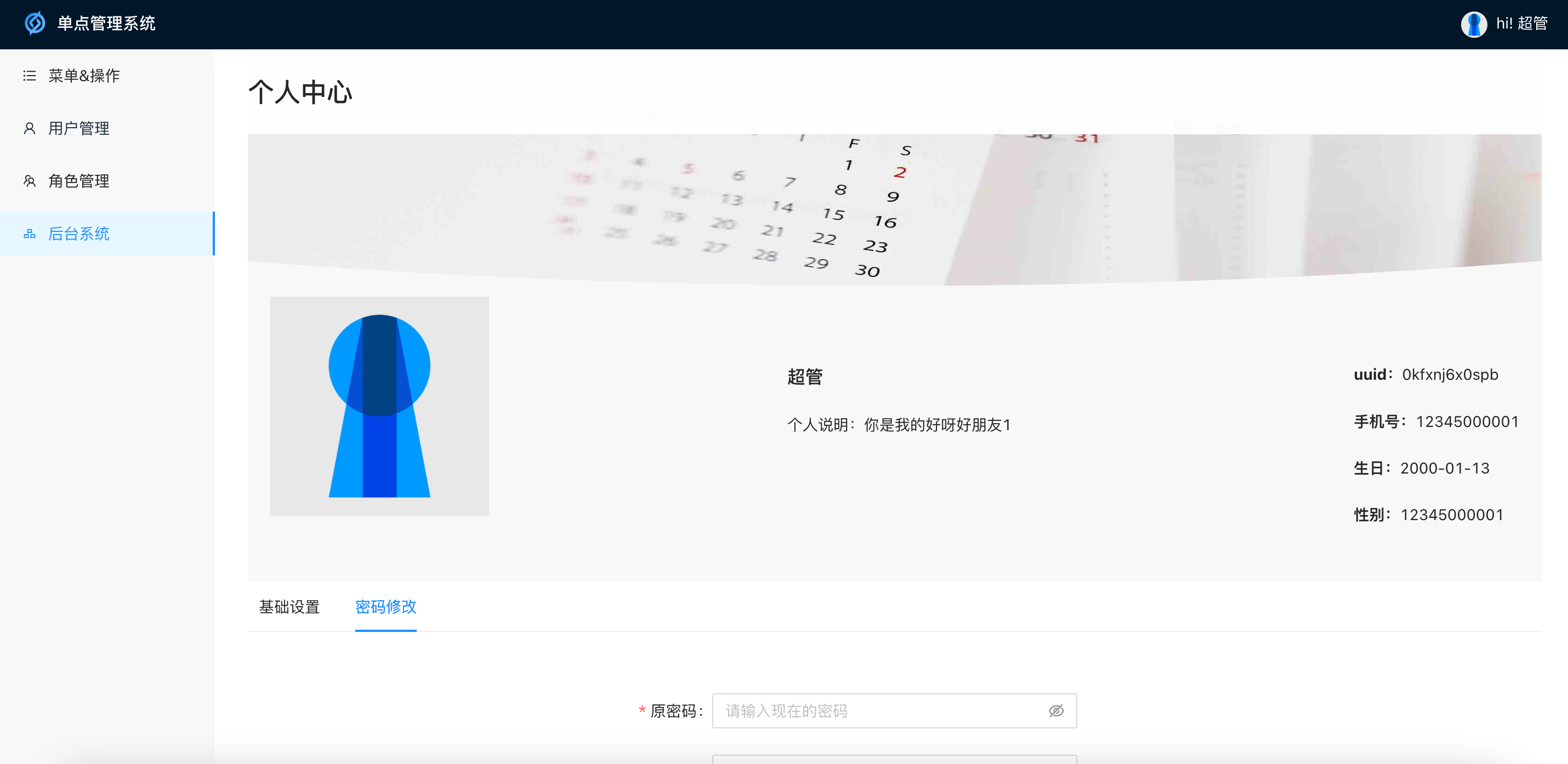
Personal center: Modify the login user’s own avatar, password, personal description, etc.
About front-end requests
Front-end request entry, the received request headers must have the following information:
| key | illustrate |
|---|---|
| cookie | The cookie generated after login is provided by the jump page after login of gateway, which is used for login verification and authorization |
| Refer | Tell the server which page initiated the request, here use unsafe-url configuration for logs, authorization whitelist, etc. |
| x-client-env | Environment, optional values are test\ |
| x-client-service | The service name of the requested server, used to forward the request |
| x-client-system | The system name of the background system, used for authorization query |
| x-client-uri | Request the operation of the server for authorization query |
About the gateway:
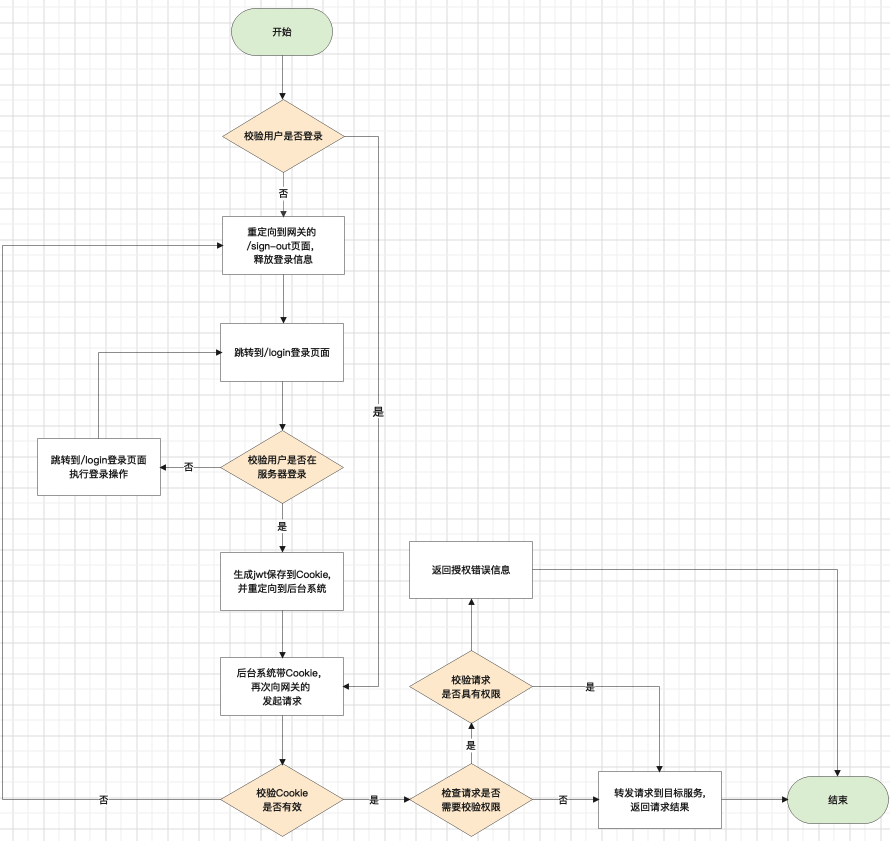
The gateway is mainly responsible for the forwarding function. In order to ensure that the generated cookie is created by the page issued by the server, the gateway also provides login, logout and login jump pages (jump to the corresponding system).
The gateway passes the headers of the request[x-client-service], Know which service to forward to, before forwarding the request, it will request the auth service, according to the cookie, it will parse the user’s information, according to the x-client-system and x-client-uri and the method that initiated the request, you can verify whether you have permission . If the verification is passed, the auth service will return the user’s uuid and name, and append them to the headers[x-origin-uuid]Parameters and headers[x-origin-name]parameter.
Systems with other single points of access
Log in to ssoms first, through系统管理Create the system, and in the菜单&操作Create corresponding pages and operations, and finally authorize users with corresponding roles.
Other systems will accept headers globally[x-origin-uuid]and headers[x-origin-name]Put it into the context, and you can directly get the user’s uuid and name in the loginc function:
uuid := l.ctx.Value(config.UUID).(string)
name := l.ctx.Value(config.Name).(string)
flow chart
deployment instructions
- import
backup.sqland execute the following sql to modify the domain name of the single-point management background:
-- identifier的值设置为单点管理后台的域名, 这边以http://ssoms.ginv.com为例
UPDATE object SET identifier="http://ssoms.ginv.com" WHERE uuid='kreppg8md1sb'
- Related services run and compile in the background
# auth
cd service/auth/api
go run auth.go
# 默认加载etc/auth.yaml配置文件,通过-f参数使用不同的配置文件,例如go run auth.go -f etc/auth.dev.yaml
# 编译生成可执行文件: go build auth.go
# ssoms
cd service/ssoms/api
go run ssoms.go
# 默认加载etc/ssoms.yaml配置文件,通过-f参数使用不同的配置文件,例如go run ssoms.go -f etc/ssoms.dev.yaml
# 编译生成可执行文件: go build ssoms.go
# ssoms vue后台
cd service/ssoms/vue
yarn install
yarn dev
# 打包前端代码: yarn build
# gateway
cd service/gateway/api
go run auth.go
# 默认加载etc/gateway.yaml配置文件,通过-f参数使用不同的配置文件,例如go run gateway.go -f etc/gateway.dev.yaml
# 编译生成可执行文件: go build gateway.go
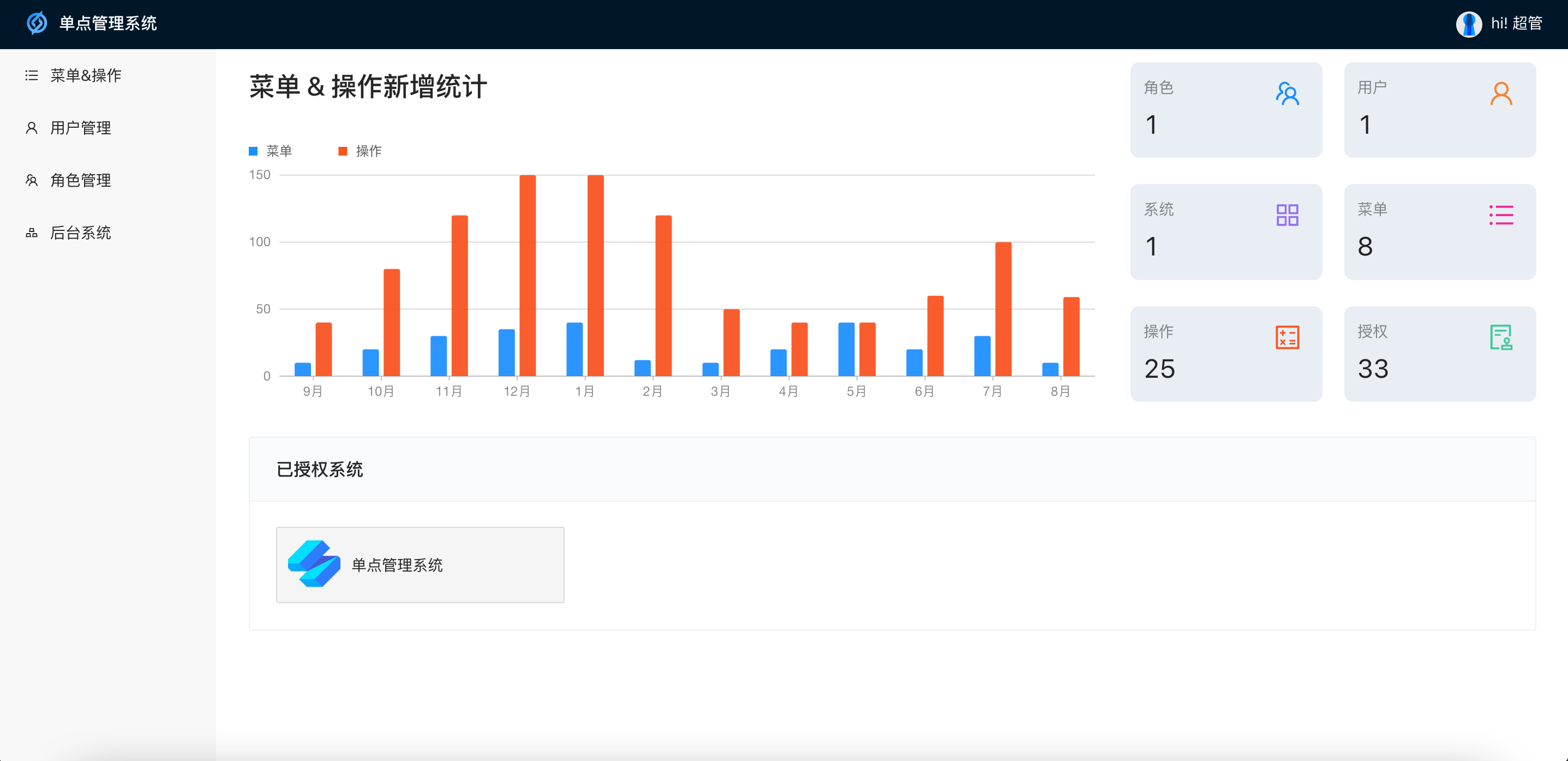
Single point management system background UI

#ginvsso #Homepage #Documentation #Download #Background #Single #Point #Management #System #News Fast Delivery