The Sysdig threat research team analyzed more than 250,000 Linux images to understand what malicious payloads are hiding in container images on Docker Hub. The results showed that 1,652 of them were identified as malicious images.
The research team collected malicious images according to several categories. The analysis focuses on two main categories: malicious IPs or domains, and secrets. Both could pose a threat to users downloading and deploying publicly available images in Docker Hub, exposing their environments to high risk.
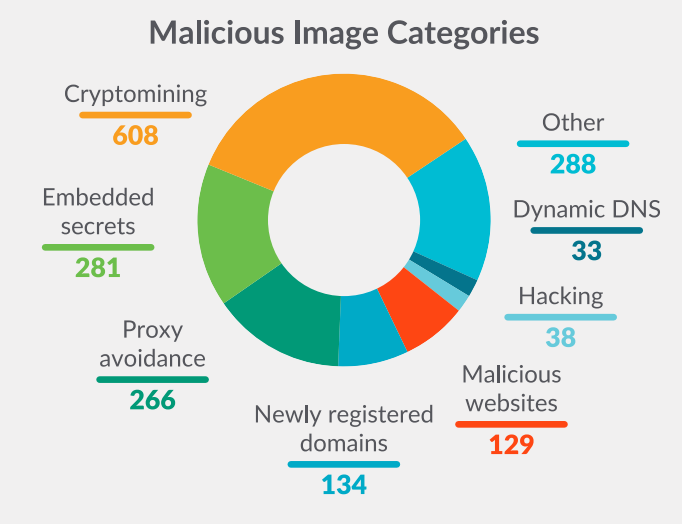
As expected, cryptomining images were the most common type,Found in 608 container images; they target server resources to mine cryptocurrency for threat actors. The second most common are embedded secrets,A total of 281 cases. This highlights the ongoing challenge of secrets management, the researchers note.
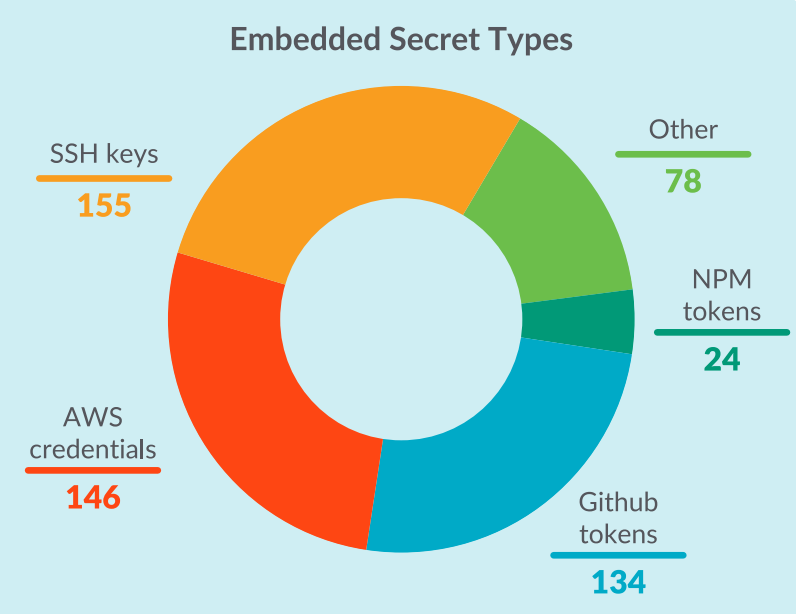
“Secrets may be embedded in the image due to inadvertent bad coding practices, or this may be intentional by threat actors. By embedding SSH keys or API keys into containers, attackers can gain access after the container is deployed Permissions. To prevent accidental exposure of credentials, sensitive data scanning tools can alert users during the development cycle.”
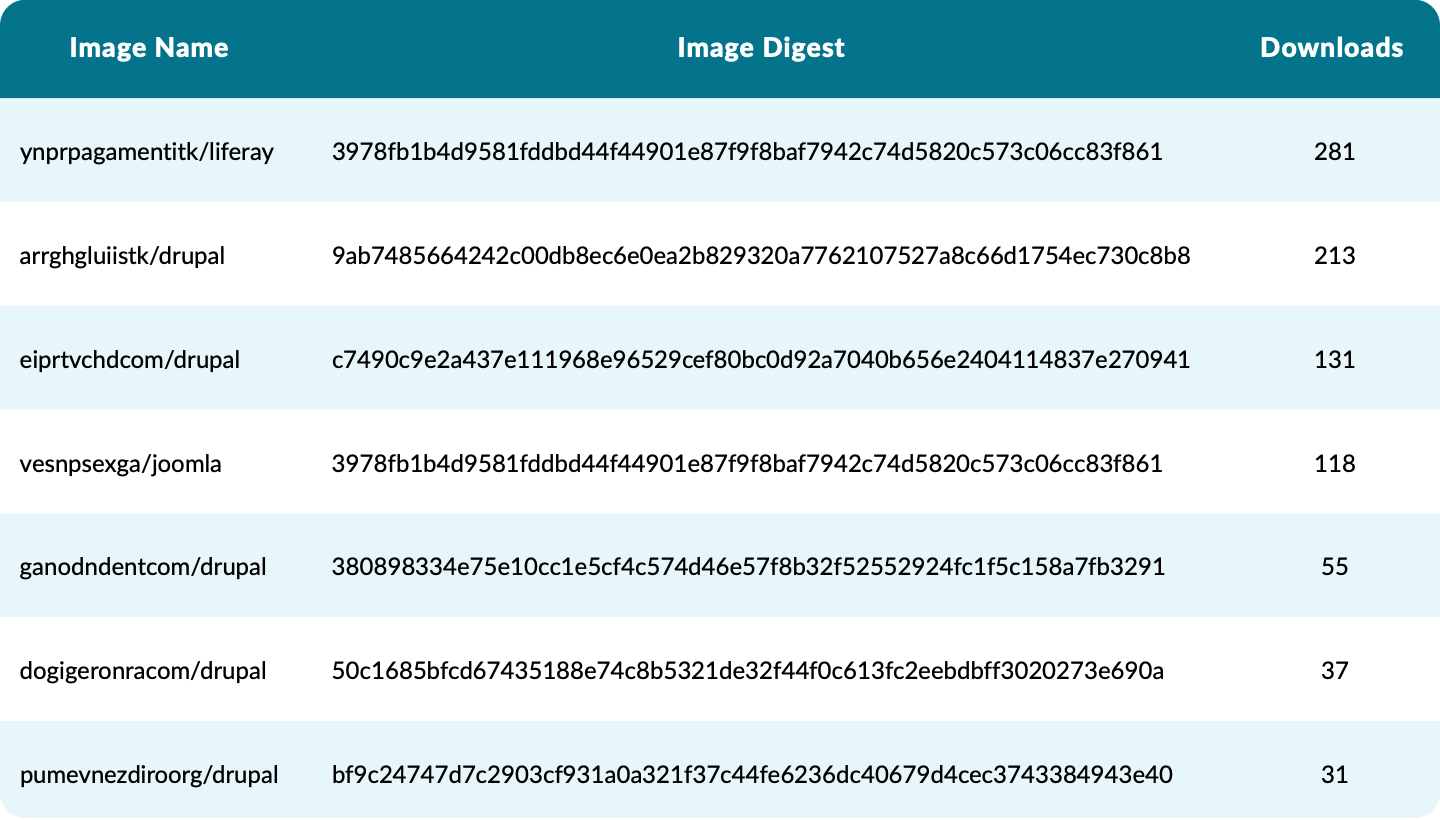
Many of the malicious images Sysdig also found used Phishing to impersonate legitimate and trusted images,To trick users into downloading and deploying, just to infect users with crypto-miners. Such errors most commonly occur when copying and pasting code or configuration from blogs or forums.

Sysdig Pointing out, it is clear that container images have become a real attack vector rather than a theoretical risk. The methods employed by the malicious actors identified in the study are specific to cloud and container workloads, and organizations deploying such workloads should ensure they have in place preventive and detective security controls in place to mitigate attacks against the cloud.
also,Looking at the statistics for 2022, 61% of all images pulled from Docker Hub come from public repositories, a 15% increase from 2021, so the risk to users is rising.This means that users love the flexibility and other features that public repositories offer, but at the same time increases the risk of exposure to malicious images.
And the size of the Docker Hub public library does not allow its operators to scrutinize all uploads on a daily basis; therefore, many malicious images go unreported. Sysdig also noticed that most threat actors uploaded only a few malicious images, so even removing risky images and banning uploaders would not have a significant impact on the platform’s threat posture.
More details can be found in the full report.
#Docker #Hub #Analysis #Malicious #Images #Hidden #News Fast Delivery