In daily production and life, we often say, “safety first” and “safety is no small matter”. Around security issues, there are solutions to various common security issues and emergency plans for unexpected security issues in all walks of life. In the field of Internet and software development, what are the common solutions to various common security problems in our daily work? Here, a combing is done in combination with the classic architecture diagram.
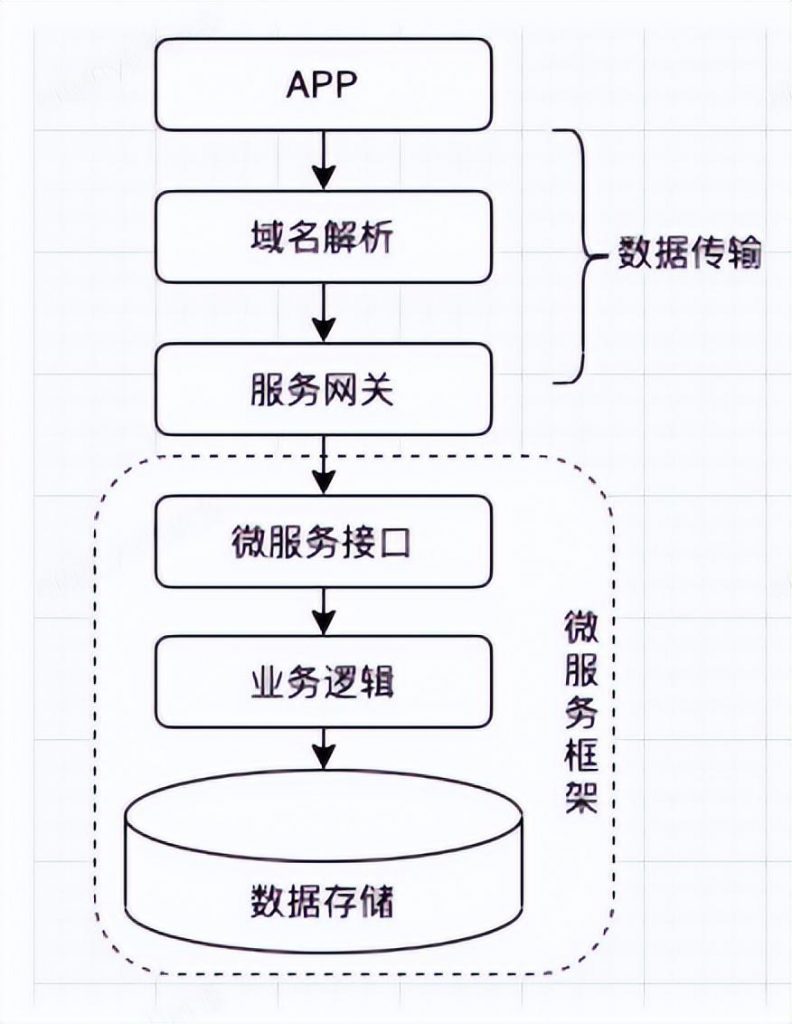
Classic Architecture Diagram
Below, combined with the above-mentioned classic architecture diagram, we analyze the possible security problems of data storage, microservice interface, external network data transmission and APP layer, and give some common countermeasures.
1 Data storage
In order to ensure the security of data storage, when storing sensitive data, it needs to be encrypted and stored. At the same time, it is recommended that sensitive data be managed in the whole company to facilitate unified management. When encrypting and storing sensitive data, common encryption methods include reversible encryption and irreversible encryption, which are respectively applicable to different sensitive data.
1.1 Reversible encryption or symmetric encryption
Reversible encryption, that is, after decrypting the ciphertext, the ciphertext can be decrypted to restore the plaintext. Symmetric encryption algorithm uses the same key for encryption and decryption. This encryption method has a very fast encryption speed and is suitable for occasions where data is often sent. The disadvantage is that the transmission of the key is more troublesome. For example, the delivery address, name, mobile phone number, etc. of online shopping are suitable for this encryption method. The commonly used symmetric encryption algorithms are DES and AES. The following uses AES as an example to illustrate the process of symmetric encryption.
In this encryption and decryption, the generation of the secret key K needs to be jointly formulated by both encryption and decryption parties and properly kept. Usually, we will store the key K in the process that needs to use the encryption and decryption program, so that it can be used directly when the program is used.
1.2 Irreversible Encryption
Irreversible encryption, that is, no need to decrypt the plaintext, such as the user’s password. Commonly used algorithms for irreversible encryption include RES, MD5, etc. Here, MD5 is used as an example for description. But everyone knows that the MD5 algorithm has collisions, that is, after different plaintexts are encrypted by MD5, the same ciphertext exists. Therefore, it is not rigorous in production to directly use MD5 to encrypt the password, and it usually needs to be used with a salt. There are also certain techniques for the use of salts. One salt value is fixed, that is, all plaintexts are encrypted with the same salt; the other is to combine specific business scenarios with a variable salt value. For example, in terms of password encryption, part or all of the user name can be used as a salt value, encrypted and stored together with the password.
2 Microservice interface
The security of microservices needs to be considered from the two aspects of request authentication and request capacity limitation. For request authentication, a method of requesting an IP blacklist can be set, and all requests to the IP are allowed or all rejected. The granularity of this method is relatively coarse. If you want to do it more fine-grained, you can perform token authentication for specific APIs, which will control more accurately than coarse-grained methods;
<jsf:consumer id="setmentService" interface="com.jd.lfsp.jsf.service.SetmentService"
protocol="jsf" alias="${jsf.consumer.alias}" timeout="${jsf.consumer.timeout}" retries="0">
<jsf:parameter key="token" value="${jsf.consumer.token}" hide="true" />
</jsf:consumer>In addition to request authentication, in actual production, the request capacity can also be limited. When the request capacity is limited, it can be limited by QPS, or the maximum number of requests per day can be limited. On the management side of the jsf platform, you can limit the QPS flow of requests for specific methods.
3 Data transfer
Data transmission is mainly divided into two parts: data requests through the front-end APP, before entering the service gateway and after entering the service gateway. After the data has entered the service gateway, it belongs to the data transmission in the computer room. Usually, this type of encryption has little meaning. For the security of such data transmission, it is necessary to establish corresponding internal security mechanisms and process specifications, and ensure it through institutional measures. Before the data enters the service gateway, what can be done for the secure transmission of the data? Before the data request enters the service gateway, we usually have transmission encryption based on the SSL protocol and HTTPS encryption that is now commonly used.
HTTPS is also a combination of HTTP and SSL protocols, so in data transmission, SSL protocol plays a crucial role. What is the working process of the SSL protocol, and how does it ensure the security of data transmission? The following is an analysis of the working process of the SSL protocol.
The authentication process between the SSL client and the SSL server is as follows:
- When the SSL client sends the random message ClientHello to the SSL server, it also sends the SSL version, encryption algorithm, key exchange algorithm, MAC algorithm and other information supported by itself;
- After the SSL server receives the request from the SSL client, it determines the SSL version, encryption component and MAC algorithm used in this communication, and sends it to the SSL client through ServerHello;
- The SSL server sends the digital certificate carrying its own public key information to the SSL client through Certificate;
- The SSL server notifies the SSL client version and the encryption component of the negotiation through the ServerHelloDone message, and starts the key exchange;
- After the SSL client verifies that the certificate sent by the SSL server is legal, it uses the public key in the certificate to encrypt the random number to generate ClientKeyExchange and send it to the SSL server;
- The SSL client sends a ChangeCipherSpec message to notify the SSL server that the negotiated secret key, encryption component and MAC value will be used in the future;
- The SSL client calculates the hash value of the exchanged handshake message, encrypts the hash value with the negotiated key and encryption component, and sends it to the SSL server through the Finished message. The SSL server calculates the exchanged hash value in the same way. And compared with the Finished message, the two are the same and the MAC value is the same, then the negotiation between the secret key and the encryption component is successful;
- Similarly, the SSL server also informs the client through the ChangeCipherSpec message that subsequent messages will use the negotiated secret key, encryption component and MAC algorithm;
- The SSL server calculates the hash value of the exchanged handshake message, encrypts the hash value with the negotiated key and encryption component, and sends it to the SSL client through the Finished message. The SSL client calculates the exchanged hash value in the same way. And compared with the Finished message, the two are the same and the MAC value is the same, then the negotiation between the secret key and the encryption component is successful;
Through the above interaction process, we can see that in the process of using SSL, in addition to the communication between the client (browser) and the server, it is difficult for any third party to obtain the negotiated key of. Even if someone who is more powerful can obtain it, based on the timeliness of users on a certain website, it will affect the timeliness of our corresponding secret keys, so the damage caused is relatively limited.
4 APP
The security problem at the APP layer needs to be solved in conjunction with the server. Here we mainly introduce the form of verification code. As a human-machine identification method, the verification code is mainly used to distinguish between normal human operation and machine operation, and block malicious behavior. In the current Internet, most systems usually require users to register in order to provide better services. After registration, users need to log in every time they use the system. During the login process, in order to prevent the illegal use of the system, the user is usually required to log in. During the login process, the commonly used verification methods are mainly through verification codes, which are currently more commonly used. There are the following types of verification codes.
4.1 SMS verification code
A form of verification code that is widely used at present. After entering a valid mobile phone number, the system sends the corresponding SMS verification code to the mobile phone number to complete the verification.
4.2 Voice verification code
By entering a valid mobile phone number, the system will complete the verification of the verification code by means of voice broadcast after calling the mobile phone number.
4.3 Picture verification code
Compared with the traditional verification code verification method, the verification code is given by the system and displayed on the page. When the page is submitted, the verification code is submitted to the system background for verification.
4.4 Semantic verification code
A relatively new form of verification code, but this method is not particularly user-friendly in comparison, and needs to be used with caution.
In addition to the above-mentioned commonly used verification codes, there are also text verification codes, puzzle verification codes, question verification codes, etc., which will not be listed here. If you are interested, you can search and learn by yourself.
This mainly analyzes some of the more common security problems and countermeasures that we encounter in daily work from the perspective of the system architecture. The security problems in actual work are far more than those mentioned here. We hope that in our daily work, all of us will tighten our security nerves, always pay attention to various potential security issues in our work, and strive to eliminate security issues before the system is released.
5 References
How SSL encrypts data in transit:
[技术每日说] – How SSL encrypts transmitted data!
Glossary:
- SSL: (Secure Socket Layer, Secure Socket Layer), a protocol layer between a reliable connection-oriented network layer protocol and an application layer protocol. SSL enables secure communication between clients and servers by mutual authentication, integrity using digital signatures, and privacy using encryption. The protocol consists of two layers: the SSL record protocol and the SSL handshake protocol.
- HTTPS: (full name: Hypertext Transfer Protocol over Secure Socket Layer), is a secure HTTP channel, simply a secure version of HTTP (HTTP+SSL). That is to say, the SSL layer is added under HTTP, and the security foundation of HTTPS is SSL, so the detailed content of encryption requires SSL.
Author: Liao Zongxiong
#Analysis #security #problems #countermeasures #system #architecture #Cloud #Developers #Personal #Space #News Fast Delivery