Wordfence, a team focused on researching WordPress security, issued a vulnerability warning today that a vulnerability in a WordPress plugin called BackupBuddy has been exploited by multiple malicious attacks since late August.
The BackupBuddy plugin, which currently has around 140,000 active installations, helps WordPress webmasters easily manage their backup operations. The plugin allows users to store backups in several different online and local directories.
The vulnerability, which has a CVE ID of CVE-2022-31474 (CVSS has a criticality rating of 7.5), is exploited in an insecure method of downloading a locally stored backup, which allows any unauthenticated user to download a backup from the server. Get any file.
This vulnerability allows an attacker to view the contents of any file on your server that can be read by your WordPress installation. These include /etc/passwd, /wp-config.php, .my.cnf, and .accesshash. These files can provide unauthorized access to system user details, WordPress database settings, and even provide authentication rights to the affected server as root.
More specifically, the plugin registers an admin_init hook for a function designed to download a local backup file, which itself does not have any checks or nonce validation. This means that the function can be triggered from any admin page, including those that can be called without authentication (admin-post.php), making it possible for unauthenticated users to call the function. Also, since the backup path is not verified, an arbitrary file can be provided and then downloaded.
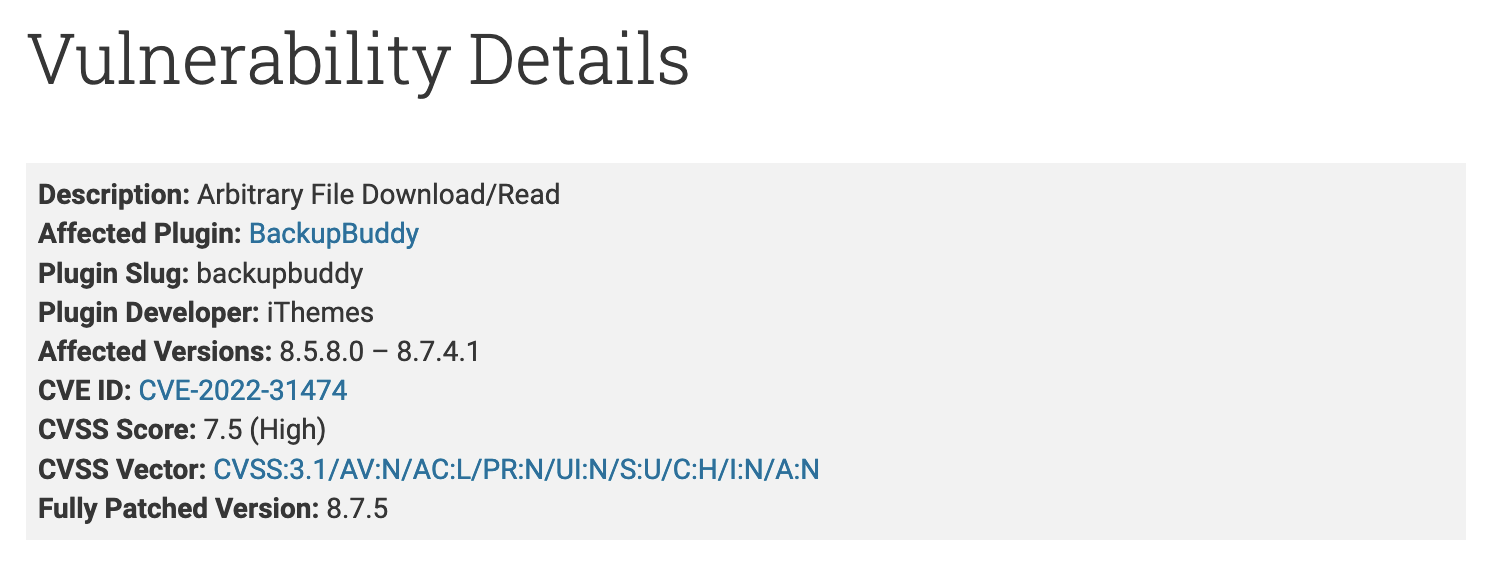
This security vulnerability affects BackupBuddy versions 8.5.8.0 through 8.7.4.1, but the vulnerability has been fully resolved in the September 2 security update (version 8.7.5).
While the vulnerability affects multiple versions of BackupBuddy, the Wordfence team found that the first attacks against the vulnerability only started on August 26 (a week before the patch was released), and there were more than 4.9 million exploits in that short period of time. attacked.
Since this is an actively exploited vulnerability, developers are strongly advised to update BackupBuddy to the latest patch version 8.7.5. The researchers also suggested that affected users can try resetting WordPress database passwords, changing WordPress salts, updating API keys stored in the wp-config.php file, and updating SSH keys, among others.
#Vulnerability #BackupBuddy #Plugin #Puts #WordPress #Users #Risk